Two-Factor Authentication
Two-Factor Authentication is the current gold standard in the industry, and naturally, Compliance Pod supports this.
Two-factor authentication (2FA), sometimes referred to as two-step verification or dual-factor authentication, is a security process in which the user provides two different authentication factors to verify themselves to better protect both the user’s credentials and the resources the user can access.
Compliance Pod allows you to set up 2FA to ask users to verify their identity on login with a unique, one-time code, sent to them via an authenticator app, text message or email. The system can be configured to demand 2FA verification from every time they log in, when they use a new browser, every X days, or a range of other options.
2FA Supporting The Security Of Your Organisation
Ensuring the protection of data is a challenge that all businesses face, in every industry, size, without fail. Our specially designed 2FA software adds an additional layer of encryption to your logins, through authenticating your login attempt with another step.
Our two-factor authentication is equipped on every one of our products because we believe every business’ data should be secure. So whether you’re looking to invest in policy and procedure management, GRC software or any of our other white label solutions we have the measures in place to protect yours and your client’s data.
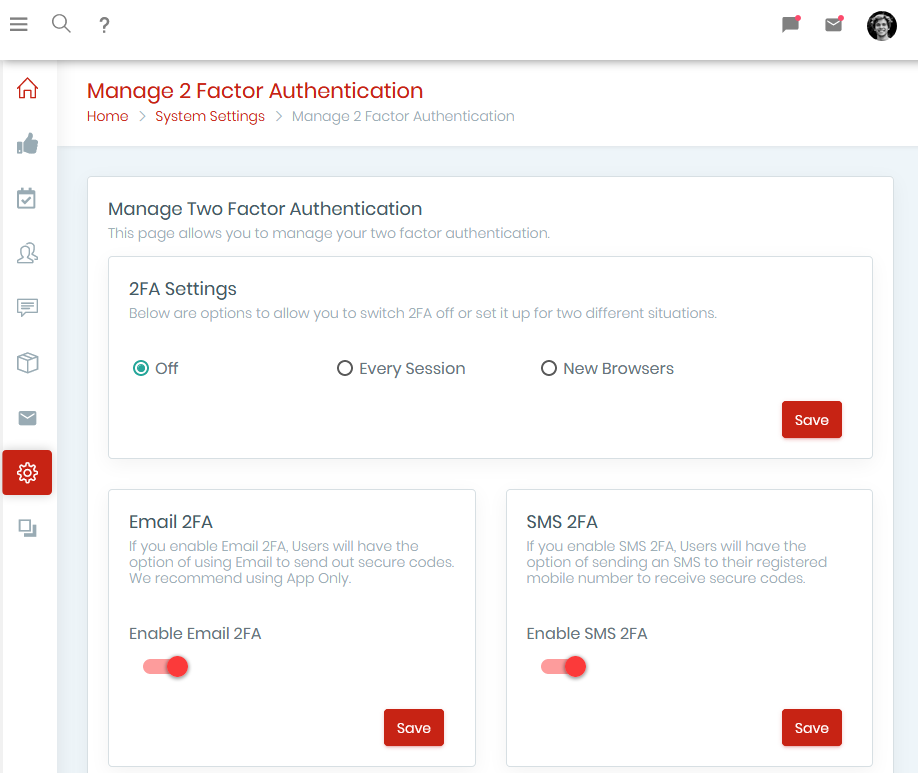
Why Do You Need Two-Factor Authentication Software?
Protect User Login Details
Keep Client Data Safe
Quick Setup Process
By implementing 2FA you’re ensuring that your user login details are kept safe and secure.
Even if a possible hacker manages to find out one of your logins, they don’t have access to the disparate second factor.
A big worry in modern times is keeping confidential information secure, especially with GDPR breathing down everyone’s necks.
An even bigger worry is ensuring the security of client data, and with two-factor authentication adds an extra layer of protection to your data.
Many of users hesitations are around how much time 2FA adds to the day to log into two accounts. The answer is none.
An initial set up takes about 10 minutes, and after that, it takes on average 2 seconds to send a verification code to your phone. Protecting your data with minimal effort on your part.
Who Could Benefit From 2FA Software?
Everyone
Client-facing Businesses
Organisations That Hold Sensitive Data
Two-factor authentication software is a benefit to anyone and everyone, regardless of the number of employees, whether client data is managed or not.
While stating everyone can benefit from 2FA sounds like a cop-out answer, the truth is adding a layer of extra security to your logins is no longer a luxury, it’s now becoming a necessity.
While data security is of the utmost importance for any organisation, client-facing companies have another layer of security they have to put in place for their customers.
Ensuring the safety of customer data helps incite trust, build stronger relationships with customers, and of course, most importantly keeps client data safe through 2FA software.
While every business possesses data, some data is more sensitive and requires much more careful attention.
Children’s data from schools, case data from law firms, patient data from GP practices, all require incredible security measures as a means to ensure the protection of confidential information.
2FA adds another layer of protection that could mean the difference between safe and compromised data.
